Eduardo Sagrera

LockBit after Operation Cronos: what it means for you in 2025 – short and to the point
Operation Cronos hit LockBit’s core in 2024, but the ransomware economy adapted; here’s what that means for your risk and defenses in…

Kagi: Finally, a Search Engine That Doesn’t Sell Your Soul (or Data)
A practical guide to Kagi’s user‑funded, ad‑free search: how it protects privacy, how to tune relevance with Lenses/Boosts/Blocklists, and how to set…

Nanochan: The Imageboard That Lives in the Shadows
This analysis examines Nanochan—an anonymous, Tor-based imageboard—with a safety-first lens for developers, enthusiasts, hackers, and curious readers. We compare its culture and…

Pitch – Where Privacy Isn’t a Feature, It’s the Foundation
This guide shows how to pitch a privacy-first product where privacy is the core architecture—not a feature toggle—delivering measurable trust for high-risk…

The New Face of Carding: Tokenized Payments and Dynamic CVV
Tokenized payments and dynamic CVV don’t just patch old holes—they change the fraud math. This analysis explains how EMV tokenization, device binding,…

Crypto Mixers After Sanctions: Adaptive Designs and Legal Battles
Sanctions forced crypto mixers to evolve. This analysis traces how designs adapted, how courts and regulators responded, what analytics can and cannot…

Satellite Internet and Anonymity: New Paths Around National Firewalls
This analysis examines how satellite internet changes the anonymity and censorship equation. It is legality-first, high-level, and avoids any evasion guidance. Executive…

Disposable Virtual Numbers: Privacy Tool or Fraudster Favorite?
Disposable virtual numbers can shield privacy or fuel abuse. This analysis balances user benefits with anti-fraud controls, regulatory obligations, and safer authentication…

Torch: One of the Oldest and Most Comprehensive Dark Web Search Engines
TORCH ONION LINK: http://xmh57jrknzkhv6y3ls3ubitzfqnkrwxhopf5aygthi7d6rplyvk3noyd.onion …
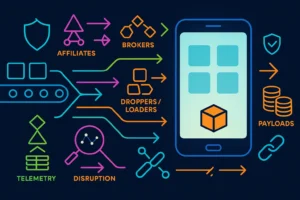
Pay-Per-Install in the Mobile Era: New Models for Malware Distribution
Mobile ecosystems reshaped pay-per-install economics, supply chains, and attribution abuse. This analysis explains the shift and emphasizes detection, disruption, and defense against…