Mobile ecosystems reshaped pay-per-install economics, supply chains, and attribution abuse. This analysis explains the shift and emphasizes detection, disruption, and defense against mobile PPI and install fraud.
From Desktop Bundlers to Mobile: How Pay-Per-Install Evolved
Legacy desktop bundlers and their decline
Pay-per-install (PPI) began as a desktop phenomenon. Affiliates drove downloads of bundled installers that packed adware, unwanted programs, and sometimes outright malware. As operating systems tightened code-signing and browser security, and major antivirus vendors expanded reputation services, the returns on desktop bundling shrank. Walled gardens matured too: modern desktop software stores, notarization requirements, and OS-level protections changed the calculus. Combined with user migration to mobile-first usage, traditional desktop PPI became less profitable and more visible to defenders.
Public policy also pressured the model. Consumer protection actions and industry coalitions pushed back against deceptive bundling disclosures and coercive consent flows. Adtech standards and browser changes throttled the affiliate arbitrage that fed desktop installers. The path of least resistance moved toward mobile, where identity, attribution, and install measurement offered new surfaces to monetize.
Rise of mobile-first affiliate networks
As app ecosystems flourished, mobile-first affiliate programs emerged around cost-per-install (CPI) and cost-per-action (CPA). Legitimate performance marketing coexisted with gray-market actors who exploited the same mechanics. Mobile operating systems provided consistent identifiers and robust attribution platforms, creating clear signals that could be gamed. PPI actors adapted, operating behind layers of brokers and “traffic partners,” while payload operators monetized access through ads, subscriptions, data exfiltration, and fraud.
Unlike desktop, mobile distribution sits inside two massive platforms with policy leverage and continuous telemetry. That concentration cut both ways: it enabled stronger enforcement, but also incentivized attackers to specialize in the quirks of attribution, install flows, and permission models unique to iOS and Android.
Why install economics shifted to mobile
Mobile devices concentrate identity, payments, and attention. A single install can yield advertising IDs, push tokens, location feeds, and monetization hooks. CPI campaigns pay on an action with clear measurement, and legitimate advertisers invest heavily in such channels. That budget gravity drew fraud, not only in the form of malicious payloads, but also in install hijacking, spoofed users, and emulator farms that siphoned attribution revenue.
Moreover, mobile devices operate continuously, producing telemetry, notifications, and background activity. For attackers, that persistence can be monetized. For defenders, it creates opportunities to detect anomalies and disrupt operations—if signals are correlated across networks, devices, and accounts.
Mobile PPI Supply Chains: Actors, Incentives, and Economics
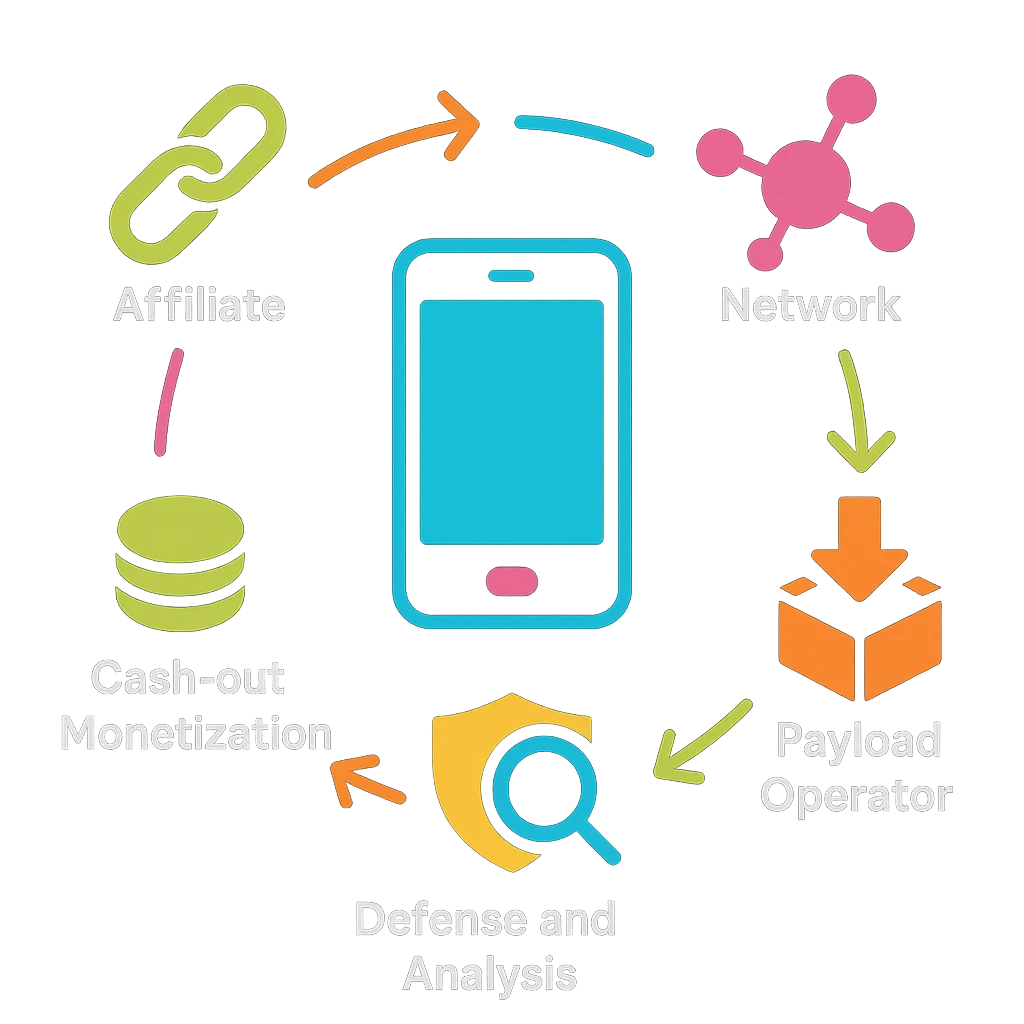
Roles: affiliates, brokers, payload operators, cash-outs
Mobile PPI ecosystems resemble layered marketplaces. At a high level:
- Affiliates source traffic, clicks, and installs through ads, promotions, and deceptive prompts. In malicious variants, they leverage sideloading, fake updates, or misleading landing pages.
- Brokers route demand and supply, abstracting relationships between traffic sources and payload operators. They optimize by geography, device model, OS version, and payout rules without disclosing sensitive details.
- Payload operators control the code delivered post-install, ranging from aggressive ad SDKs to fully malicious modules. They monetize via ads, subscriptions, fraud, or data resale, often swapping payloads dynamically.
- Cash-outs occur through ad revenue, affiliate payouts, or secondary fraud (e.g., premium services). Money movement is obfuscated via chains of accounts and intermediaries.
Pricing models: CPI, CPA, rev-share, and hybrid
PPI intersects with legitimate performance marketing models:
- CPI (cost per install) pays when an app is installed, creating incentives for volume and measurement gaming.
- CPA (cost per action) ties payment to a post-install event—registration, subscription start, or purchase—encouraging deeper fraud against attribution systems.
- Revenue share splits future monetization, incentivizing longer persistence, broader permissions, or abusive ad stacking.
- Hybrid models mix CPI with CPA to balance risk, but can unintentionally reward stealth and persistence that cross policy lines.
In gray-market contexts, operators leverage these models to disguise malicious intent as aggressive growth marketing. Brokers exploit information asymmetries across advertisers, ad networks, and measurement providers.
Incentive misalignment and fraud loops
When payouts depend on measured installs or actions, attackers target the measurement surface. Click injection, device resets, and emulator farms create artificial conversions. The result is a fraud loop: fake installs trigger payouts; payouts fund more traffic; advertisers raise budgets to “sustain growth,” unwittingly paying for abuse.
Defenders can break this loop by aligning incentives around verified quality. Measurement providers, ad networks, and app stores must coordinate on signals and sanctions. Without shared telemetry and policy enforcement, fraud loops escalate and spill into user harm, including malicious permissions and deceptive subscription flows.
Distribution Vectors on Smartphones: Beyond the App Store
Sideloading and third-party app stores
Outside official storefronts, sideloading expands the attack surface. Third-party stores, drive-by APK prompts, and “update” pages are common vectors in public reporting. Where platform protections allow user-controlled installation, attackers layer social engineering on top of permissive settings. Even within official stores, policy circumvention and cloned listings appear periodically; however, platform review and takedown pipelines reduce dwell time compared to unvetted channels.
Enterprise distribution features can also be abused by untrusted actors when organizations do not enforce strict MDM posture and certificate controls. This underscores the need for device policy baselines and verified app sources.
Malvertising and deceptive install prompts
Malvertising blends legitimate ad inventory with deceptive creative and landing pages that push unwanted installs. Tactics include fake system alerts, misleading “required update” prompts, and interstitials that crowd out safe options. Because ads traverse complex supply paths, accountability can be diffuse, making enforcement slow unless platforms and supply-side partners share signals.
Measurement spoofing and click hijacking often accompany malvertising, ensuring that attribution flows back to the offending affiliate even when the user had different intent.
Trojanized SDKs and supply-chain risks
SDKs embedded by developers can introduce risk when they include hidden capabilities, undisclosed data flows, or update channels outside app store review. Public research has documented cases where third-party libraries evolved from benign to abusive over time, or where compromised SDK distribution delivered malicious variants. This supply-chain angle lets attackers piggyback on legitimate developer relationships and organic installs.
Developers should vet SDK vendors, follow secure update practices, and adhere to standards like the OWASP Mobile Application Security Verification Standard (MASVS) for supply-chain hygiene. App stores and ad networks can reinforce this by auditing SDK behavior and enforcing disclosure requirements.
Affiliate Tracking and Attribution Abuse in Mobile Campaigns
Click injection and install hijacking
Attribution platforms assign credit based on last-touch rules, click timestamps, and app install events. Attackers abuse this by injecting clicks just before installation completes, or by hijacking deep links to appear as the source of the install. In some historical cases, apps with excessive permissions listened for signals that an install was underway and then fired a synthetic click to capture credit. Defenders counter with secure timestamps, fraud scoring, and deduplication across networks.
Device fingerprinting and ID resetting
When platform-provided advertising IDs are restricted or reset, some actors resort to probabilistic device fingerprinting. Others automate ID resets to create multiple “unique” users from one device. Both tactics distort campaign measurement and can cross policy lines. App stores and measurement providers increasingly penalize ad ID misuse and fingerprinting, encouraging privacy-preserving measurement while improving fraud detection.
Fake installs, bots, and emulator farms
Bot-based installs and emulator farms attempt to simulate user acquisition and post-install events. These operations create telemetry gaps: device models that never appear on carrier networks, improbable time-to-install distributions, or uniform behavior across supposed users. Cross-correlating network, device, and behavioral signals can expose synthetic activity and support takedown actions.
Stealth and Persistence Tactics Used by Mobile Malware Installers
Abusing accessibility and overlay permissions
Accessibility and overlay permissions are powerful for legitimate use cases yet attractive for abuse. Public reports describe misuse for clickjacking, credential interception, or hiding UI elements. Platform policies restrict these permissions and require clear disclosures, but attackers may obfuscate their purpose, request at opportunistic moments, or defer requests until trust is established.
Droppers, loaders, and delayed activation
Installers may function as droppers that later fetch additional modules, or as loaders that activate dormant capabilities upon triggers such as time, connectivity, or user actions. Delay tactics aim to evade initial review and avoid immediate detection. Dynamic payload swaps further complicate static analysis and signature-based detection.
Evasion of app store review and mobile AV
Actors attempt to evade automated and manual review by gating behaviors behind server-side flags, geofencing, or staged capability unlocks. Mobile AV and runtime protections respond with behavioral analysis, reputation feeds, and policy-driven enforcement. Because app stores control distribution, coordinated telemetry and rapid response can curtail dwell time once patterns emerge.
Detection, Disruption, and Defense Against PPI in Mobile Ecosystems
Network-level signals and telemetry correlation
Defenders gain leverage by correlating install telemetry with network indicators. Outbound connections immediately after install, repeated lookups of the same endpoints across supposed “unique” devices, and anomalous TLS fingerprint reuse can reveal orchestrated activity. Coordinated sharing between app stores, ad networks, and security vendors accelerates takedowns and reduces false positives.
Where permissible, enterprises can baseline typical app behavior and alert on spikes in data egress, suspicious domains, or encrypted channels that diverge from known SDK patterns. Aggregated, privacy-preserving analytics help separate organic growth from fraud-driven spikes.
Mobile MDM policies and least-privilege controls
Mobile device management (MDM) and endpoint detection and response (EDR) can enforce least privilege. Policies that restrict sideloading, require vetted app catalogs, and limit high-risk permissions lower exposure. NIST and CISA guidance emphasize configuration baselines, patch currency, and strong identity measures to mitigate mobile threats without sacrificing usability.
Attribution hygiene and fraud analytics
Advertisers and measurement providers can raise the bar with fraud analytics that scrutinize time-to-install distributions, improbable click-to-install paths, and device-ID churn. Cross-network deduplication prevents affiliates from claiming the same install multiple times, while strict enforcement against fingerprinting and ID reset abuse aligns incentives. Independent audits grounded in MRC guidance and IAB Tech Lab standards further improve trust in the supply chain.
Risk mitigation checklist for defenders
- Network telemetry and correlation: Baseline post-install network behavior; flag clusters of identical TLS fingerprints, DNS patterns, or endpoints across “unique” devices.
- Mobile EDR/MDM baselines: Enforce no-sideloading policies; require app notarization/signing; restrict high-risk permissions (accessibility, overlays) to approved apps.
- Least privilege: Review permission requests during app onboarding; use managed configurations to disable unneeded capabilities.
- Store policy enforcement: Monitor developer behavior changes (package name churn, frequent SDK swaps); report violators to stores with reproducible, non-sensitive evidence.
- Attribution hygiene: Implement cross-network deduping; monitor abnormal time-to-install, install bursts at off-hours, and ad ID reset anomalies.
- Fraud analytics: Apply invalid-traffic scoring in line with MRC guidance; require transparency from partners on traffic provenance and filtering.
- User education: Warn against installing from unknown prompts; teach permission hygiene; promote official store use only.
- Enterprise controls: Maintain allowlists for corporate devices; audit SDK inventories in first-party apps; implement incident playbooks for suspicious installs.
Case Studies from Public Research and Law Enforcement Actions
Notable Android campaigns documented by researchers
Public reports across recent years describe mobile campaigns that abused ad attribution, permissions, and subscription flows. Common threads include deceptive updates, sideloaded app portals, and trojanized SDKs. Measurements often cite anomalous device clusters, click-to-install manipulations, and dynamic payload delivery post-approval.
Researchers emphasize that transparent SDK disclosures, store policy enforcement, and cooperative telemetry sharing can significantly reduce campaign dwell time. Patterns like geofenced activation and time-delayed behaviors appear frequently in post-incident analyses.
Takedowns targeting affiliate malware rings
Law enforcement and platform-led operations have dismantled affiliate rings by combining financial tracing, domain seizures, and partner coordination. Public statements highlight the importance of ad ecosystem collaboration—advertisers, measurement firms, and app stores—to sever payouts and block distribution. These actions reinforce deterrence by raising the cost and lowering the lifetime of malicious campaigns.
Lessons learned for platform guardians
- Measurement is a security boundary: if incentives are tied to measured actions, attackers target the measurement layer.
- Supply-chain transparency matters: SDK audits and strict update disclosures disrupt covert capability changes.
- Coordinated response wins: cross-stakeholder signal sharing enables faster, more precise enforcement.
Policy, Compliance, and Ethical Considerations in the Mobile PPI Era
Legal exposure under cybercrime and fraud statutes
PPI schemes that rely on deception, unauthorized access, or abusive billing can trigger criminal and civil liability under computer misuse, wire fraud, and consumer protection laws. Participants risk investigation, civil penalties, or prosecution. Even nominally “marketing” operations face exposure if they manipulate attribution, spoof users, or violate platform terms. Compliance teams should treat attribution integrity as a legal risk area, not merely ad ops hygiene.
Advertising standards and app store policies
App store policies prohibit deceptive behavior, unauthorized permissions, and hidden functionality. Advertising standards bodies and measurement councils provide guidance on invalid traffic and transparency. Aligning internal practices with these policies reduces both fraud exposure and reputational risk. Violations can result in developer bans, app removals, and clawbacks of advertising payouts.
Responsible disclosure and community coordination
When researchers discover abusive patterns, responsible disclosure to app stores, SDK vendors, and measurement providers accelerates remediation. Coordinated disclosure timelines and clear, non-sensitive evidence help stakeholders fix issues without spreading operational details that could aid copycats. Community-driven taxonomies and shared indicators (handled ethically and lawfully) improve collective defense.
Glossary of Key Terms
PPI, CPI, CPA, attribution, install farm
- Pay-Per-Install (PPI): A model where affiliates are paid for delivering app installs; abused when installs are coerced or fraudulent.
- Cost-Per-Install (CPI): Legitimate advertising model paying for installs; targeted by fraud to siphon payouts.
- Cost-Per-Action (CPA): Payment for a defined post-install event; fraud seeks to simulate these events.
- Attribution: Process of crediting installs/actions to marketing touchpoints; a prime target for manipulation.
- Install farm: Scaled operation (often using emulators or low-cost devices) to fake user acquisition.
Dropper, loader, overlay, accessibility abuse
- Dropper: An app that fetches or enables additional payloads after initial installation.
- Loader: Component that activates hidden capabilities or modules under certain conditions.
- Overlay: A UI layer drawn over other apps; abused for clickjacking or concealing prompts.
- Accessibility abuse: Misuse of accessibility APIs to read or inject actions without clear user consent.
Device fingerprinting, IDFA/GAID, MDM
- Device fingerprinting: Probabilistic technique to identify devices via signals like OS, fonts, and network attributes; disfavored by platform policies.
- IDFA/GAID: Apple and Google advertising identifiers; intended for ad measurement with user controls.
- MDM: Mobile Device Management; enterprise tooling that enforces configuration, app allowlists, and policy.
FAQ
What is pay-per-install and how does it differ from cost-per-install advertising?
PPI describes affiliate-driven install monetization that may include gray or malicious distribution. CPI is a legitimate ad pricing model used by reputable advertisers and networks. The difference lies in the business context and compliance posture: CPI follows platform rules and measurement standards, whereas PPI abuse manipulates attribution or delivers harmful payloads.
Why did PPI shift from desktop to mobile, and what changed technically?
Desktop protections, user migration, and policy pressure reduced returns on bundlers. Mobile offers steady identifiers, centralized app stores, and constant user engagement. Technically, mobile attribution systems and permission models created new surfaces for manipulation and monetization—while also enabling stronger platform-led detection and takedown.
Which distribution vectors are most cited in public mobile malware reports?
Public reporting frequently cites sideloading via deceptive prompts, malvertising, and trojanized SDKs within legitimate apps. Official stores also encounter periodic policy violations, but review and enforcement shorten dwell time compared to unvetted channels.
How do attackers game mobile attribution and what signals can expose it?
Common tactics include click injection, install hijacking, ad ID resets, and emulator-driven fake users. Signals that expose abuse include improbable click-to-install timings, device clusters sharing network fingerprints, and repeated endpoint patterns across “unique” devices. Cross-network deduplication and invalid-traffic scoring help isolate anomalies.
What legal risks do participants in PPI schemes face?
Participants risk civil and criminal liability under fraud, computer misuse, and consumer protection laws. Violations of app store and ad network policies can trigger bans, clawbacks, and economic loss. Legal exposure grows when users are deceived, data is exfiltrated, or billing is abused.
How can organizations detect and disrupt PPI-driven campaigns against their users?
Correlate network telemetry with install events, enforce MDM baselines, audit SDKs, and engage attribution hygiene: dedupe across networks, monitor ad ID churn, and flag abnormal install bursts. Coordinate with platforms to report patterns using non-sensitive, reproducible evidence.
What role do app stores, ad networks, and SDK vendors play in mitigation?
App stores enforce policy and remove violators. Ad networks and measurement providers filter invalid traffic, share fraud signals, and penalize misattribution. SDK vendors must maintain transparent disclosures and secure update channels. Together, these stakeholders can dismantle fraud loops by aligning incentives and sharing telemetry.
References and Further Reading
Public research highlights
- ENISA Threat Landscape reports: https://www.enisa.europa.eu/publications/enisa-threat-landscape
- OWASP Mobile Application Security Verification Standard (MASVS): https://mas.owasp.org/MASVS/
- OWASP Mobile Top 10: https://owasp.org/www-project-mobile-top-10/
Official policies, standards, and advisories
- Google Play Developer Policy Center: https://play.google.com/about/developer-content-policy/
- Apple App Store Review Guidelines: https://developer.apple.com/app-store/review/guidelines/
- NIST SP 800-53 Rev. 5 (Security and Privacy Controls): https://csrc.nist.gov/publications/detail/sp/800-53/rev-5/final
- NIST SP 800-63 (Digital Identity Guidelines): https://pages.nist.gov/800-63-3/
- NIST SP 800-124 Rev. 2 (Mobile Device Management): https://csrc.nist.gov/publications/detail/sp/800-124/rev-2/final
- CISA Mobile Device Security Best Practices: https://www.cisa.gov/secure-our-world/mobile-device-security
- IAB Tech Lab app-ads.txt: https://iabtechlab.com/standards/app-ads-txt/
- Media Rating Council (MRC) Invalid Traffic Guidelines: https://mediaratingcouncil.org/invalid-traffic-detection-and-filters-guidelines
- GSMA Mobile Security resources: https://www.gsma.com/security/
Law enforcement and regulator resources
- Europol IOCTA: https://www.europol.europa.eu/publications-events/main-reports/internet-organised-crime-threat-assessment-iocta
- INTERPOL Cybercrime: https://www.interpol.int/How-we-work/Combatting-cybercrime
- CISA advisories and guidance: https://www.cisa.gov/resources-tools
Read the full analysis and share responsibly. Subscribe for research-based updates on disrupting mobile PPI and install fraud.
- Key takeaways:
- Mobile PPI thrives where attribution and incentives are misaligned; defenders should treat measurement as a security boundary.
- Supply-chain transparency—especially around SDKs—reduces covert capability changes and helps stores enforce policy.
- Correlated telemetry across networks, devices, and attribution systems enables faster detection and takedown.
- MDM baselines and least-privilege permissioning materially reduce exposure to abusive install flows.
- Cross-industry cooperation, guided by official standards and policies, breaks fraud loops and raises attacker costs.